Zero Trust
Change is a given.
Unknown change is a threat.
Unknown change is a threat.
It's a Zero Trust world.
Creating strong perimeters to keep the "bad guys" out is outdated, particularly when you have resources residing in hybrid environments or completely outside your security perimeter.
In 2021, the White House released an executive order mandating a shift to zero trust principles.

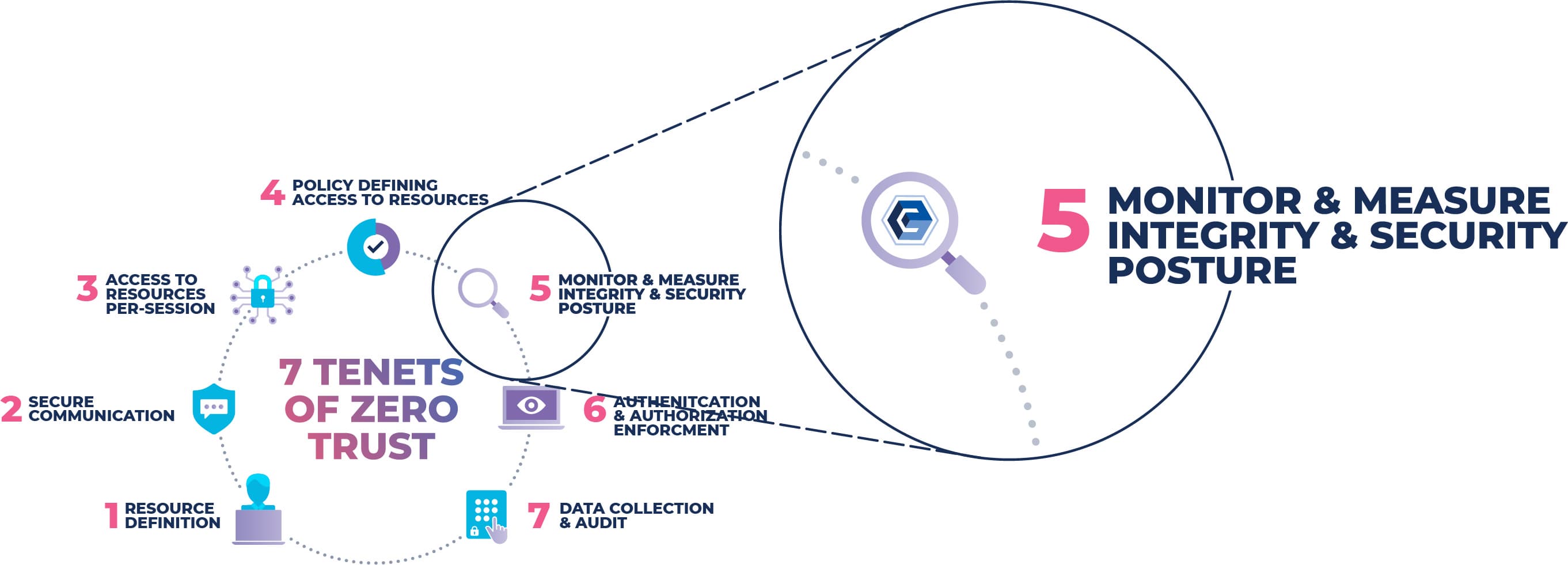
The Guiding Principles of Zero Trust
NIST SP 800-207 Principles of Zero Trust
The guiding principles of Zero Trust focus on users, assets, and resources. For those areas of focus, the 7 tenets of Zero Trust were created to help guide organizations with a Zero Trust strategy.

ASSUME BREACH
Assume a malicious presence is inside the environment at all times and implement security controls to minimize impact.
VERIFY - DON'T TRUST
Organizations should continuously verify all components within their IT infrastructure to ensure no compromise has occurred.
LEAST PRIVILEGE
Once verified, users, devices, and services should be granted the minimum possible access and time period required to complete their function.
However, there's a concerning gap in the popular discourse around Zero Trust.
Most Zero Trust solutions over-focus on access and authentication.
A Zero Trust Architecture should eliminate assumed trust throughout an IT environment.
This requires enforcing dynamic cybersecurity policies across four layers:
Identity layer
Device/workload layer
Access layer
Transaction layer
The 4 Requirements to Ensure Integrity
- An authoritative baseline of what data should look like.
- A means of identifying and protecting data from unauthorized change.
- A mechanism to roll back unauthorized changes not blocked at the source.
- A way to verify that controls 1-3 are functioning correctly

What's missing in most vendors' Zero Trust Solutions? Integrity.
Arm yourself.
Download The Missing Components of Zero Trust today to elevate your security posture and avoid making the most common Zero Trust mistakes.

Tenet 5: The Most Overlooked Tenet of the Zero Trust Framework
Tenet 5 focuses on keeping all critical assets in a state of integrity: the assurance that your assets are uncorrupted and can only be accessed or modified by those authorized to do so.
CimTrak is the only software that meets the requirement of Tenet 5: The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
CIMTRAK INTEGRITY SUITE
Benefits of implementing the
CimTrak Zero Trust Integrity Suite.
Automatically identify zero-day malware, exploits, and malicious behaviours.
Reduce Mean Time To Identify (MTTI) breaches from months to seconds.
Prevent integrity drift in real-time, while automating incident response.
Rapidly scale security and IT architecture with minimal human effort.
Without integrity management controls in place, you can't have a true zero trust architecture.
Zero Trust Gap Analysis
How does your current Zero Trust tool address these required elements?
Most tools only focus on authentication, authorization, logging, and micro-segmentation.
You most likely don't have integrity monitoring in place:
- Visibility & communication across all subjects, assets, and resources
- Change monitoring & management
- Allowlist permissions
- Configuration enforcement
A Zero Trust Gap Analysis will identify all potential points of improvement in your IT environment.