CimTrak for Docker and Containers
Docker Host and Container Security

How CimTrak Helps
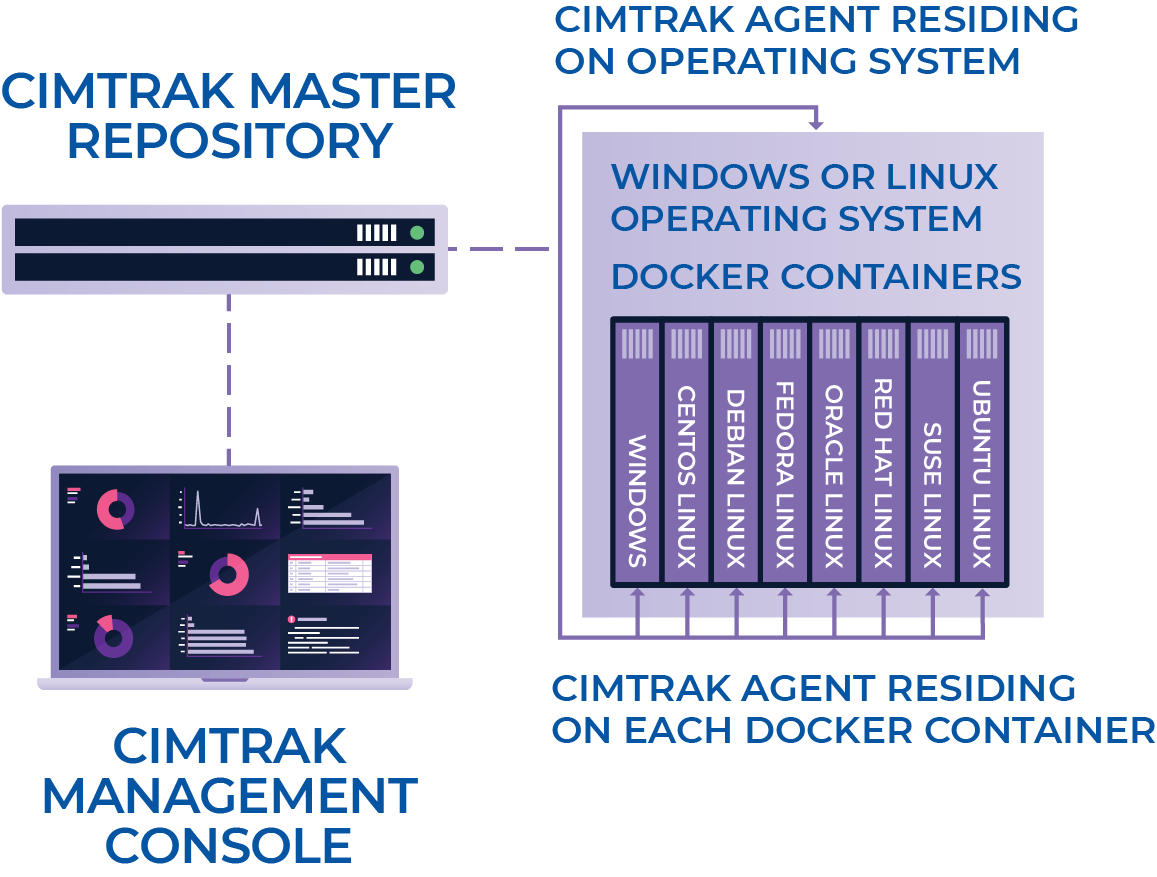
CimTrak can easily be deployed when creating a Docker container and allows for the monitoring of the host OS as well as critical files and data that may reside in the container.
This provides users with the same level of situational awareness of changes that are occurring, just as CimTrak does for other servers.
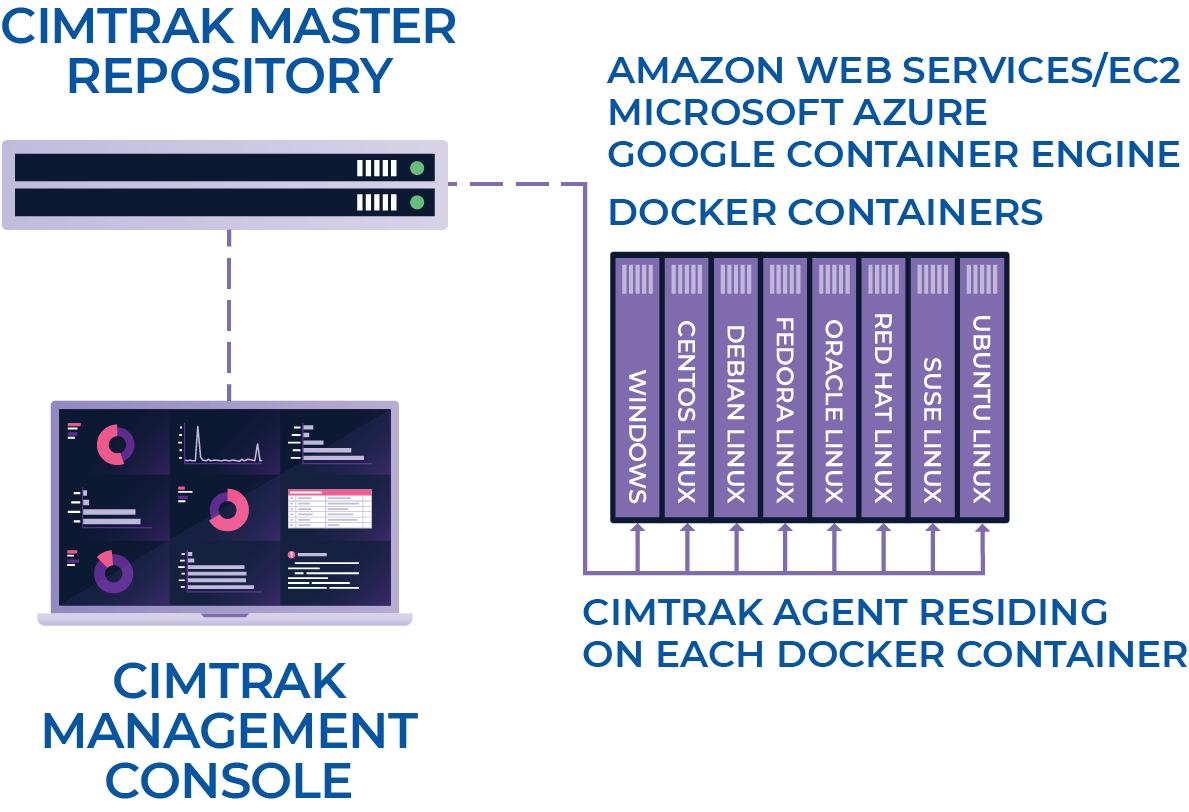
Docker containers deployed in cloud environments such as Amazon Web Services (AWS), Microsoft Azure, or Google Container Engine can also be monitored.
CimTrak ensures a strong IT security and compliance posture is continuously monitored for unexpected changes. This minimizes risk and provides assurance that Docker hosts and Docker containers are in a constant state of integrity.
Benefits of Using CimTrak for Docker Security
Easy deployment to Docker containers
Ensures IT security and compliance
Quickly identifies malicious change
Simple management interface
Securing a Docker Environment
With the ability to quickly deploy and scale, many IT professionals are starting to utilize containers within their environments. However, Docker security is often overlooked due to the transient nature of containers, which often lulls users into a false sense of security. The reality is that IT security risk still exists with Docker hosts and containers, regardless of their life expectancy.
Learn More:
Download the Report!

A few examples of how traditional security tools would not detect or identify a problem resulting from malicious change(s) to containers:
Action : The threat actor gains root access to the Docker host
Impact: When the threat actor gains access to the host, this gives access to anything on the host.
Action : The threat actor stops and removes all running containers
Impact: When the threat actor stops and removes all running containers, the production applications and systems they power are now down and gone forever, with all the data lost.
Action : The threat actor modifies an existing production image
Impact: When the threat actor modifies existing production images, the production containers won't have the expected baseline, nefarious changes will now be in every container that uses that image.
Action : The threat actor starts new containers with the infected image
Impact: When the threat actor starts a new container with the infected image, the user may not know or recognize that they were changed. Now, the live production containers are actively infected and could be stealing data or worse.
Action : The threat actor modifies the docker network assigned containers
Impact: When the threat actor modified the docker network, it opened up access to more subnets to the outside world, leaving the production docker host vulnerable to the entire internet.