A proven track record of delivering a resilient security posture to small, mid-market, and enterprise companies.
300,000+
servers covered
95%+
Less change noise
1,000's
Companies secured
Countdown Until the Next
CimTrak Walkthrough Wednesday
Join us every Wednesday for a walkthrough of CimTrak including a live Q&A
USE CASES
Deploy CimTrak across your security stack to enhance monitoring, auditing, and change control processes .
Reduce the cost and complexity of detecting and remediating security problems resulting from unintended changes to your infrastructure in real-time.
CIMTRAK DELIVERS CONTINUOUS SECURITY & AUTOMATED COMPLIANCE
Secure your entire IT infrastructure.
Identify threats before they hit.
Built-in threat intelligence provides additional context to determine is change is authorized.
Trusted File Registry
Reduce change noise and prevent false positives from known and good vendors that brings focus only to potentially malicious changes.
STIX/TAXII Thread Feeds
Protect yourself from malware and threat hashes via a blacklist that's updated 24/7/365.
File Reputation
Integrate with Virus Total, Palo Alto Wildfire, or Checkpoint’s Threat API, to perform real time file and malware analysis of file changes.
Change reconciliation workflow & reporting.
Easy-to-use tool for managing change from the initial identification of the change to reconciling if the change was authorized and remediating if unwanted.
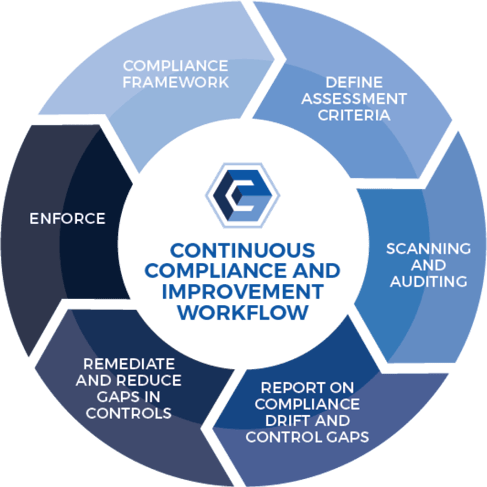
Continuously comply with major regulatory requirements.
Quickly establish, maintain and fix compliance requirements that improve the overall security and audit-readiness of your IT infrastructure.





CUSTOMIZED DEMO
Secure your IT infrastructure and stay compliant with CimTrak.
What you can expect:
- Discuss your security, compliance, and operational needs.
- Live demo focused on your needs/requirements.
- Activate your free trial: 1-1 white glove setup and install













