Change is the nemesis of IT and cybersecurity professionals who need to maintain a secure and available environment. No matter how secure your environment is, a single bad change is all it takes to open the door to a bad actor.
Unauthorized, unexpected, and unwanted changes to critical files, systems, and devices can quickly open a gaping hole in an organization’s cybersecurity posture. It doesn’t matter how good the rest of its controls are at that point—a breach may be imminent.
What is a Change?
Everything that happens in an IT environment starts with a change: a file, configuration setting, or device is altered, deleted, added to, or even just read by a user or service.
Every bad thing in an organization’s environment begins with change — but so does every good thing. The challenge lies in determining the difference. This is also where a trusted baseline comes into play. Anything not included in the baseline can be assumed bad until proven otherwise.
For each change, an organization can follow a simple process:
- Determine precisely what changed in the environment.
- Check whether the change is authorized under the baseline.
- Allow, block, or roll back the change as appropriate.
Tony Sager, SVP and Chief Evangelist at The Center for Internet Security (CIS) explains it like this:
“You need to know what you have and what changes are acceptable. Then you have to stop everything else and manage by exception where necessary. It’s not necessarily easy because there’s lots of change. If you have the machinery to control this, you have the basis of integrity.”
Why is Change So Important?
As we’ve seen, all bad things in an IT environment begin with change. This fact is clarified by IDC research, which found that a huge proportion of IT outages are caused by human error, including failure to conform to change management processes. In other words, failure to properly manage change in an IT environment is among the largest causes of unplanned downtime.
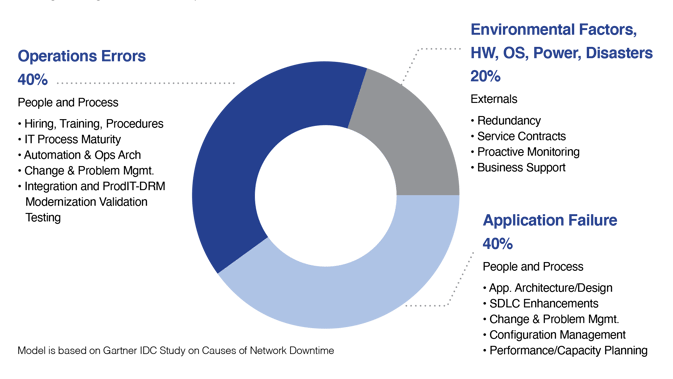
Donna Scott, VP and Research Director at Gartner, goes a step further by stating that:
“80 percent of unplanned downtime is caused by people and process issues, including poor change management practices, while the remainder is caused by technology failures and disasters.”
Based on their experience working with hundreds of IT organizations, the authors of The Visible Ops Handbook note that even once an incident has occurred, 80% of Mean Time To Recovery (MTTR) is wasted on non-productive activities—notably, determining which change is responsible for the outage.
Managing Change as a Cybersecurity Function
A study commissioned by the U.S. Department of Defense (DoD) determined that:
“Information security hinges on the effectiveness of the change management process. As a result, we need to implement a detective control to verify compliance [with an authoritative baseline] and take decisive action when the process is not followed.”
Notice the wording. Change management isn’t just important—it’s the lynchpin of the entire information security function. With all this in mind, why hasn’t there been an attempt by cybersecurity vendors to address change management?
Change Management is the process of making decisions about your network, which is informed by a combination of effective security policy and change monitoring. An effective change management process ensures that the right person can access the right information at the right time. Implementing a strategy that closely follows Zero Trust principles can be a step in the right direction.
System Integrity Assurance (SIA)
As a completely different approach to cybersecurity, System Integrity Assurance (SIA) focuses on the fundamentals. Instead of trying to identify and categorize all bad things, it identifies everything that is allowed (including changes) in an environment and blocks everything else.
Some level of management by exception is needed, of course. Some changes may not be included in the baseline, but they could be deemed acceptable on further analysis. In these cases, the change can be allowed and added to the trusted baseline for future use.
Through this process, system integrity assurance verifies integrity, giving organizations complete control over changes in their environment.
This begs another question:
What happens if you know every time something is added, removed, or changed in your environment, you stop anything that isn’t authorized… and you expand this capability across all asset classes?
- Ransomware and other malware can’t run in the environment.
- Attackers can’t traverse the network or exfiltrate data.
- Nobody can change files or configurations to make them dangerous or non-compliant.
- Users can’t accidentally run malicious attachments.
- Nobody (even privileged administrators) can alter critical system files.
This approach takes away a massive proportion of the threats that can arise in an IT environment with minimal human involvement.
To find out exactly how System Integrity Assurance (SIA) addresses the major issues in cybersecurity, download the Authoritative Guide to System Integrity Assurance.

December 12, 2024




