In Ransomware: Part I, we learned what ransomware is and why you should be aware of these attacks which are hurting both large and small IT infrastructures. In Ransomware: Part II, we will dig a little deeper, letting you know the "how" to fight against it.
The Battle of Ransomware
Ransomware is spreading like wildfire and is not slowing down anytime soon. Congressmen Reps. Ted Lieu, D-Calif., and Will Hurd, R-Texas have shed light on the differences between ransomware attacks and other breaches, noting how ransomware can potentially impact patient safety by making patient health data inaccessible to clinicians in the health industry. Though this blog may be a little more technical in nature than others, it will provide insight into the fight against ransomware. As ransomware is sweeping the world in every industry there needs to be a solution, and CimTrak offers more than one.
How to stop Ransomware
CimTrak Agent’s “Deny Access Mode” will stop all file additions, removals, or modifications. Regardless of what permissions a user might have or what type of account you are logged in with, no person or process will be able to change your files.
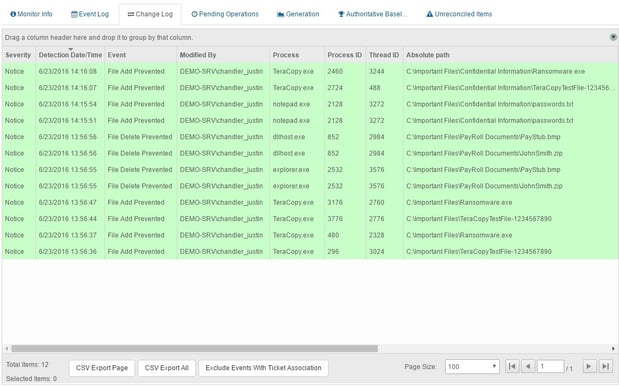
This can be easily set up by creating CimTrak monitoring rules on files and directories that you feel are extremely critical and never should be stolen, deleted, encrypted, or hacked by these ransomware attacks. At any time, a user can disable the mode to make approved changes, then reenable the protection after approving the changes. Below, is an example in CimTrak’s Event Log, showing how the CimTrak Agent actually blocked certain attempted file changes.
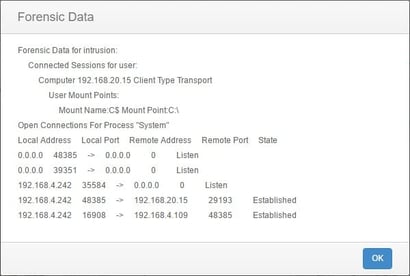
These same events could be sent off to Email, SMS, Syslog, or SIEM solutions, so that you are notified immediately if ransomware attempts to steal your data, providing you with forensic data for each event.
What About Dynamic Files?
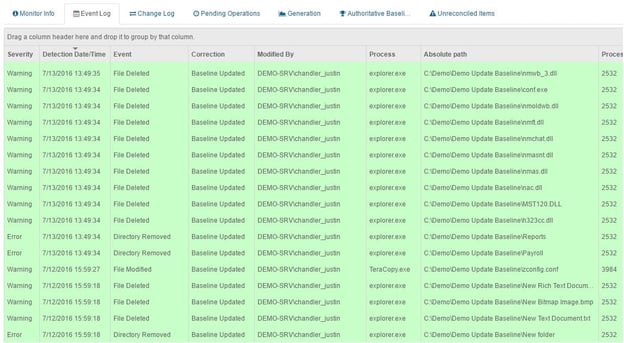
Sometimes, we need files to be able to change dynamically. Data files are a good example. In this case, we have another alternative to combat ransomware. It is called Update Baseline Mode. As changes occur, CimTrak will automatically update the baseline and create “snapshots” of your file system continuously every time something changes. That way if any of those changes were detrimental, unwanted, or infectious; you will have the opportunity to roll back to any baseline that was created manually or automatically. This will take you right back to the point BEFORE any ransomware hit. Or maybe you just want to revert to your last good configuration or your “golden image”.
Since CimTrak stores a copy of your files within the encrypted and secure Master Repository, you will always have the opportunity to revert back to the state right before the cryptolocker or ransomware encrypts all of your files rendering them unusable. You can also download a separate copy of your snapshot to maybe back up elsewhere.
Is this a good file or a bad file?
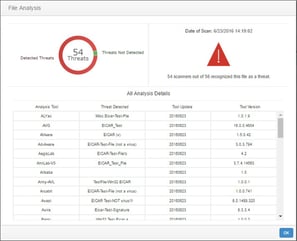
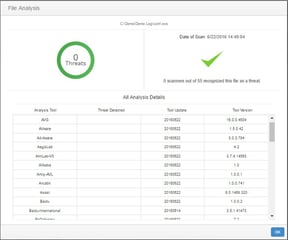
CimTrak now has integration with the VirusTotal, a subsidiary of Google. VirusTotal identifies viruses, worms, trojans, and other kinds of malicious content detected by antivirus engines and website scanners. Normally you may have 1 or 2 anti-virus tools in your infrastructure. However, there are many tools out there and they each have their own large signature-based databases that differ. That is the beauty of using VirusTotal as it consolidates the largest and most popular anti-virus tool databases to one website. You can easily right-click a file within CimTrak and analyze the file to see if it is a threat or not.
This file will be checked amongst 55+ anti-virus tools. This greatly helps users understand not only what is changing in their environment but if these files are risks or not.
With the help of CimTrak, you can combat ransomware and cryptolockers, gaining real-time insight into exactly what has changed throughout your entire network. From databases to network devices, Cimcor enables IT teams to achieve full oversight and mitigate risks.
Download our technical summary to learn more about CimTrak today.
Tags:
Cybersecurity
July 26, 2016