Would you rather deal with the aftermath of a raging fire in your business, or install fire extinguishers and a sprinkler system? The choice is obvious: The proactive measure is by far the better option of the two. You should take this same approach to your cybersecurity efforts.
In the face of a cybersecurity event, your organization could face challenges like lost profits, lost customer trust, and lost resources. A recovery plan is needed in the event of a breach, but you should also enact proactive cybersecurity measures to prevent a breach from occurring in the first place.
Learn why reactive cybersecurity efforts are not enough in the current market and explore the advantages of proactive cybersecurity measures in this post. We will also cover four top strategies you can use to make your cybersecurity efforts more proactive.
Reactive vs. Proactive Cybersecurity Measures
Before we examine the four proactive cybersecurity measures to consider for your business, let us first discuss proactive cybersecurity measures more broadly. Why is it so important to be proactive?
Defending against breaches before they occur is critical because of the damage a breach can cause to your business. Breaches can result in lost profits, lost productivity, and the lost trust of your customers and community.
Related: Podcast: Applying a Proactive vs Reactive Mindset
The average time it takes to uncover and contain a breach is 277 days. If imagining the amount of damage an attacker could deal to your network in that amount of time is enough to make you sweat, you already understand the importance of being proactive in your cybersecurity efforts.
Let's examine some of the methods you can use to proactively secure your organization’s data and prevent breaches before they occur.
4 Proactive Cybersecurity Measures to Implement Today
- Enact basic security measures aligned with modern best practices
- Perform regular network monitoring to identify suspicious activity and vulnerabilities
- Conduct cybersecurity awareness training to educate your team on cyber attacks and best practices
- Engage in penetration testing to assess and strengthen your organization’s defenses
1. Enact Basic Security Practices
The first measure in our list is a bit of a “catch-all.” This contains all the measures you may have seen in other posts—in other words, the basics. One of the simplest proactive measures you can take is to practice good cybersecurity hygiene in your organization.
Related Read: 5 Cybersecurity Tips to Improve Employee Habits
Some basic security measures you will want to ensure your organization takes include:
- Implementing multi-factor authentication
- Requiring employees to use strong passwords for all accounts
- Installing a firewall to protect your perimeter
- Regularly updating all software and devices to the latest version
Many organizations stop their proactive cybersecurity measures with these practices. However, in today’s security landscape, the basics may not be enough. If you truly want to protect your organization’s data, you will need to explore the other measures in this article.
2. Perform Regular Network Monitoring
Another proactive measure to consider is regular network monitoring. Network monitoring is an automated process that allows you to track devices and traffic, helping you identify suspicious activity and potential vulnerabilities.
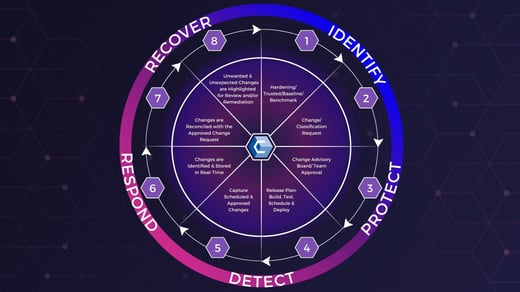
Consider implementing a file integrity monitoring solution to assist you with these efforts. A solution like CimTrak can take your file integrity monitoring efforts to the next level. In addition to logging employee activity in your network and enabling you to search for irregular behavior, you can also use CimTrak to automatically roll back unauthorized changes or return to a snapshot of previous settings.
Implementing a Zero Trust Architecture (ZTA) is another excellent way to assist with network monitoring efforts. By segmenting your employees and providing the minimum level of access each user needs to perform their job duties, you can reduce the mean time to identify a breach (MTTI) from months to seconds. For more information about implementing Zero Trust in your organization, reference our post: ANSWERED: How To Implement Zero Trust in Your Organization.
3. Conduct Cybersecurity Awareness Training
Even the strongest technological defenses can crumble in the face of social engineering attacks and insider threats. This inherent vulnerability is why conducting regular cybersecurity awareness training is vital for organizations.
Related Read: 5 Essential Email Security Tips for Businesses
Educate your team on common cyber attacks and best practices for defending against a breach. Some topics you may want to consider regular training for your employees include:
- Phishing
- Malware
- Ransomware
- Password Hacking
Cybersecurity isn’t just the responsibility of your information security team—it’s every employee’s responsibility to ensure they are doing their part to protect your organization’s data. Regular training will encourage this mindset among your employees.
4. Engage in Penetration Testing
The last measure you might take in a proactive approach to cybersecurity is to engage in penetration testing. In penetration testing, you will work with white hat hackers. These trusted experts will play the role of attackers, testing your organization’s defenses.
You may choose to use a white hat hacker to probe your network for vulnerabilities. The penetration testing will reveal any holes in your defenses, which you can then patch.
How To Implement Proactive Cybersecurity Measures
Reactive cybersecurity measures aren’t sufficient in the current environment. Cyberattacks become more sophisticated each year, and to maintain compliance and adequately protect your organization, you need to take a more proactive approach.
Implementing the four measures discussed in this post will help your organization recover from cyberattacks and actively repel and prevent them. By maintaining strong security hygiene and educating staff, you prepare your systems and employees to defend against a breach. Penetration testing can help you identify potential vulnerabilities, and regularly monitoring your network allows you to identify and defend against a breach quickly.
Network monitoring can be tedious at the best of times. To cut through the noise and allow your IT team to focus only on the alerts that matter most, try a file integrity monitoring solution with system integrity assurance like CimTrak.
See an instant preview of CimTrak today to see how our solution can help your organization be more proactive in its cybersecurity measures.
Tags:
Cybersecurity
March 18, 2025



![Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]](https://www.cimcor.com/hs-fs/hubfs/Cybersecurity%20Lifecycle.jpg?width=520&height=294&name=Cybersecurity%20Lifecycle.jpg)