Enterprise-level organizations have access to a vast range of security tools, resources, standards, and advice. Utilizing free and paid threat feeds, they can gain an unprecedented level of insight into the latest threat actor tactics, techniques, and procedures.
Even small organizations find themselves surrounded by a laundry list of compliance requirements, risk management frameworks, and regulations.
All considered it may seem as if the tasks needed for organizations to identify ways to protect against cyber attacks would be easy. However, much of this information can easily become overwhelming. Budgets and logistics can make it a challenge to do everything — or even come close — leaving organizations to make tough decisions about which actions/controls to prioritize. This is where the CIS Basic Controls come in.
What are the CIS Basic Controls?
CIS Basic Controls are the foundational level of the globally accepted CIS Controls framework — a defense-in-depth set of 20 best practices developed by a broad range of IT and cybersecurity industry experts.
The CIS Controls are designed to help organizations identify the actions they need to take to defend against the most common real-world attacks. To further break down the order in which they should be implemented, the 20 CIS Controls are broken down into three categories:
-
Basic Controls: Controls 1-6
-
Foundational Controls: Controls 7-16
-
Organizational Controls: Controls 17-20
As part one of this three-part series, we will begin with the Basic Controls.
Overview of the Six CIS Basic Controls
The CIS Basic Controls are many times considered cybersecurity 101. These are security controls every organization may want to implement prior to others, as the ROI on the Basic controls can be higher than other cybersecurity activities.
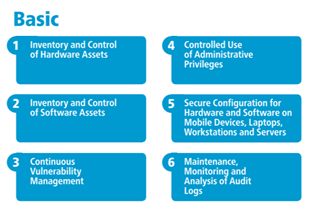
Image Source: cisecurity.org
Multiple studies have demonstrated that implementing only the first five basic controls is enough to protect organizations against 85% of all cyber attacks.
CIS Control 1. Inventory and Control of Hardware Assets
“Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.”
WHY IS THIS IMPORTANT?
Threat actors don’t always attack targets where they are strongest — they often look for weak points. Some of the most common weak points in a business network are new or unprotected devices that may not have the latest security patches or are already compromised.
These assets are easy to find using a variety of scanning technologies, so insecure devices are a huge security risk even if they are only connected to an organization’s network for a short period of time. If an attacker has already gained access to a target network, they may even be able to exploit weaknesses in machines that are not connected to the Internet. Maintaining oversight of hardware assets on your network is essential as this maintenance enables the quick identification and removal of unauthorized assets that could otherwise be exploited.
HOW TO IMPLEMENT
Most organizations use one or more automated tools to identify hardware assets. Ideally, this process should take place in real-time to enable the prompt removal of unauthorized assets. Whether or not automated tools are used, organizations must also maintain an up-to-date asset inventory to keep track of relevant hardware assets — even when they are not connected to the network.
CIS Control 2. Inventory and Control of Software Assets
“Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that all unauthorized and unmanaged software is found and prevented from installation or execution.”
WHY IS THIS IMPORTANT?
Exploiting vulnerable software assets is among the most common ways for a threat actor to compromise a target network. Similar to hardware, vulnerable software assets are easy to find using scanning technologies, and they are also susceptible to malicious software distributed via email and compromised websites.
Ultimately, the only way to prevent attacks against vulnerable software assets is to ensure that assets are routinely updated with the latest security patches. For that to be possible, an organization must have a detailed, up-to-date inventory of every software asset on its network(s).
HOW TO IMPLEMENT
Most organizations use automated scanning tools to keep track of software assets, which should ideally happen in real-time. Whether or not automated tools are used, a register of all identified software assets must be maintained. When unauthorized assets are identified, immediate action should be taken to remove them.
CIS Control 3. Continuous Vulnerability Management
“Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.”
WHY IS THIS IMPORTANT?
One of the most challenging aspects of cybersecurity is the speed with which new threats are developed. Whenever a vulnerability is identified in a piece of software or hardware, threat actors race to ‘weaponize’ it before organizations can remediate — sometimes even before vendors have time to release a patch. Hardware and software assets that are secure one day could easily become a liability the next — and this a true every single day of the year.
To combat this, the third Basic CIS Control requires organizations to continuously scan their environments for new vulnerabilities, and quickly remediate them where they arise. Since a huge proportion of cyber attacks are designed to exploit known vulnerabilities, implementing this one control can help organizations achieve a massive reduction in cyber risk.
HOW TO IMPLEMENT
Even for small organizations, manually checking for new vulnerabilities and implementing patches is close to impossible. Instead, the vast majority of organizations use automated scanners to identify vulnerabilities within their environment. Many organizations also use patch management tools to ease the implementation, testing, and (where necessary) rollback of patches.
CIS Control 4. Controlled Use of Administrative Privileges
“The processes and tools used to track/control/prevent/correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications.”
WHY IS THIS IMPORTANT?
Misuse of administrative privileges is another of the most common ways that threat actors compromise target networks. This can be achieved either by tricking a legitimate user into running a malicious executable or by ‘cracking’ the password of an account with administrative privileges.
By tightly controlling administrative privileges — e.g., by limiting privileges to a ‘need only’ basis and promptly deleting accounts that are no longer needed — organizations can make it much harder for threat actors to gain access to an admin account.
HOW TO IMPLEMENT:
A combination of built-in operating system controls and custom scripts can provide organizations with the information needed to ensure admin accounts aren’t being misused. This should be combined with strict processes for new or leaving users to ensure account privileges are kept to the minimum needed for each role, and disused accounts are deleted promptly.
CIS Control 5. Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
“Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.”
WHY IS THIS IMPORTANT?
When new assets — from operating systems and servers to smartphones — are deployed, by default everything is turned on. All ports are open, and all services/applications are enabled. This is helpful from a deployment and ease of use perspective, but bad news for security.
Threat actors can easily scan for asset configurations that are known to be insecure, making poorly configured hardware and software assets a huge liability. This Control prompts organizations to ensure all assets are configured for security, and that configurations are tracked over time to ensure new vulnerabilities are not introduced.
HOW TO IMPLEMENT:
Since any single asset could have thousands of configuration options, even the smallest organizations couldn’t hope to comply with this control manually. Instead, organizations use industry-standard configuration guidelines such as the CIS Benchmarks as a guide. For widely used operating systems, many organizations also use CIS Hardened Images, which drastically speed up the implementation of securely configured assets.
However, even with these tools, maintaining secure configuration across all assets can be extremely challenging. For this reason, an increasing number of organizations use automated tools to assess configuration over time and create alerts when vulnerabilities are introduced.
CIS Control 6. Maintenance, Monitoring, and Analysis of Audit Logs
“Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.”
WHY IS THIS IMPORTANT?
While many organizations retain logs for compliance purposes, many do not consistently analyze logs in search of malicious activity. Without a strong process for analyzing system logs, attackers can hide inside an organization’s network for extended periods of time without being noticed. This type of access is often used to systematically steal sensitive information.
HOW TO IMPLEMENT:
Log management tools are commonly used to record and store system logs. However, in many cases, those logs are rarely (if ever) thoroughly analyzed. Security Incident and Event Management (SIEM) tools often include analysis functionality, and can usually integrate with other technologies such as threat intelligence feeds to further improve the analysis process.
Implement CIS Basic Controls with CimTrak
CimTrak is an IT integrity, security, and compliance toolset that can help aid with the implementation and maintenance of the CIS Basic Controls. Continuously monitoring an environment by detecting changes to assets, files, and accounts, CimTrak provides alerts and reports, making it easy for organizations to identify security issues in hardware and software assets.
INTEGRITY VERIFICATION AND ASSURANCE
The process of continuous detection, interpretations, and the management of change/deviations to an expected state of operation is also known as Integrity verification and assurance. CimTrak eliminates change "noise" that can be overwhelming, by pinpointing unauthorized, unwanted, and unexpected activities in real-time creating and establishing a resilient and trusted infrastructure. This is integrity verification and assurance. With this process, CimTrak is able to help mitigate identified CIS vulnerabilities. Should a vulnerability be introduced due to a change, CimTrak provides the alert and guidance for risk remediation.
Using CimTrak your organization can:
-
Scan your environment to identify all hardware and software assets and determine whether those assets are known and permitted. (CIS Controls 1 and 2)
-
Continuously scan your environment for new vulnerabilities — including those created by configuration or file changes — so they can be remediated before a threat actor has time to exploit them. (CIS Control 3)
-
Create and enforce whitelists to control which accounts and processes can make changes to files. (CIS Control 4)
-
Track and report on the security configuration of all assets in real-time and get instant notifications and remediation advice whenever a new issue is detected. (CIS Control 5)
-
Automatically collect, manage, and analyze audit logs to detect, understand, or recover from cyber-attacks. (CIS Control 6)
CimTrak utilizes CIS Benchmarks to continuously assess your infrastructure for vulnerabilities and to ensure that systems are in a hardened state. Mapped to the CIS Controls the results of these CIS Benchmark tests provide you with powerful evidence that you have implemented a CIS Control or CIS sub-control. With advanced reporting, CimTrak enables you to know where you are at in the process of implementing CIS Controls.
To find out more about how CimTrak can help your organization align its security strategy and processes with CIS Controls, download the solution brief today.
Tags:

July 2, 2020



