Many organizations have treated FIM as shelfware for years.
They maintain their FIM contracts to satisfy compliance requirements, of course. But, for the most part, their security teams ignore any change alerts the FIM tool creates.
There’s a simple reason for this…
Legacy FIM Has 3 BIG Problems
There are actually three major reasons for this:
- Noise
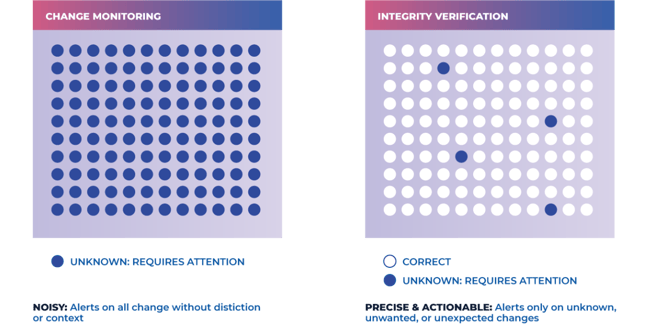
Legacy FIM tools create lots of alerts… but provide zero context. This has the effect of overwhelming security teams while providing no real value. Imagine (or perhaps you don’t have to) coming into work on Patch Tuesday to see thousands of alerts, most of which—if not all—relate to completely legitimate and trusted changes. There’s no realistic way of triaging all of these alerts without context, so in most cases, they are ignored en masse.
- Lack of integrity assurance
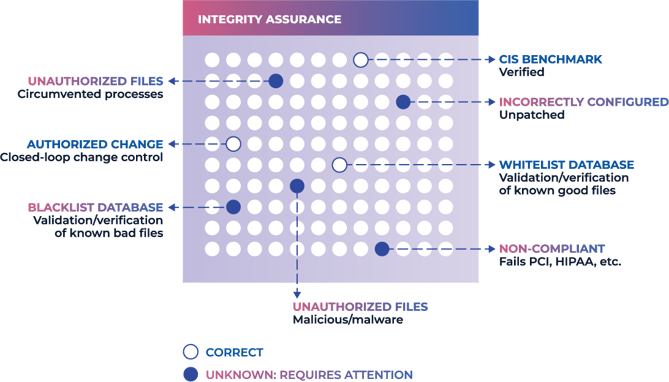
Integrity assurance establishes a trusted and authoritative baseline of what’s allowed to be and happen in an IT environment, and then prevents, limits, or rolls back everything else. Whenever an unknown change occurs, it’s managed by exception. Acceptable changes are added to the baseline, while dangerous changes are prevented.
Legacy tools provide basic file monitoring but no integrity verification. This leaves security teams unable to distinguish between legitimate and dangerous changes, leaving (most of the time) to simply ignore change alerts.
- Resource intensive
Legacy tools identify change using daily polling scans. This process is highly resource-intensive, so it usually happens overnight. While that may seem logical, it creates a huge risk: dangerous changes are often undetected for many hours.
File Monitoring vs. File Integrity Monitoring
If you look closely at how legacy FIM tools work, you’ll see that they don’t provide File Integrity Monitoring at all—they provide basic file monitoring.
Integrity is the accuracy and completeness of data throughout its life cycle. No matter what service, device, or user accesses, stores, processes, transmits, or receives data, it must remain accurate and complete. This requires four essential integrity controls:
- An authoritative baseline in line with system hardening best practices.
- A way to protect data from unauthorized change.
- A way to roll back unauthorized changes not blocked at the source.
- A way to verify that controls 1 - 3 are in place and working correctly.
While legacy FIM provides only basic monitoring and alerts, Next-Gen File Integrity Monitoring solutions provide genuine integrity verification. This has two major benefits:
- Drastically reducing change noise, as the solution can identify and allow legitimate changes.
- A huge positive impact on security and risk management, as malicious or dangerous changes are identified and prevented/rolled back automatically.
What Are Next-Gen File Integrity Monitoring Tools?
Next-Gen File Integrity Monitoring software is a huge step forward from legacy FIM tools. Instead of basic file monitoring, Next-Gen FIM provides genuine file integrity checking, verification, and enforcement for all files and data—without creating unnecessary noise.
Next-gen FIM tools follow a three-step integrity verification process:
- ALLOW legitimate changes without human intervention.
- BLOCK or ROLL-BACK known dangerous or malicious changes automatically.
- ALERT ONLY on unexpected, unknown changes.
In other words, next-gen FIM tools automate a huge proportion of the change management process—only requiring human analysts to get involved with a small number of unexpected, unknown changes. And once those changes have been categorized, they will also be handled automatically in the future.
This process is possible because Next-Gen FIM tools don’t rely purely on denylists. Instead, they combine three levels of verification to prevent bad changes while cutting out change noise:
- Complete register of all files, including those held by hardware and software, along with their correct states, configurations, and settings.
- Allowlist of trusted file hashes, metadata, and configurations to validate and verify data integrity and authenticity.
- Denylist of known bad file hashes from external threat feeds, file reputation services, and malware data repositories.
By combining these three elements, integrity verification tools enforce integrity across IT environments while simultaneously suppressing change noise by 95%.
File Monitoring and Integrity Verification in Real-Time
As we’ve already noted, legacy FIM tools rely on daily polling scans—which usually happen at night. This can leave organizations vulnerable to the impact of malicious or dangerous changes for up to 24 hours at a time, giving attackers time to cause damage, traverse the network, or steal data.
Next-Gen File Integrity Monitoring tools monitor for changes and verify file and data integrity in real-time. This provides two huge benefits:
- Respond Instantly to Attacks
Known bad changes are prevented or rolled back automatically. E.g., if a configuration setting is changed out of compliance with CIS Benchmarks, the tool can instantly reverse the change. Incident responders can triage unknown changes quickly without wasting time on “noisy” false positives.
- Save Network Resources
Next-Gen tools scan the environment once to establish a baseline, then receive change data from agents and modules across the environment. This process is highly efficient and barely registers on the resource monitor.
Mitigate Security Risks with Next-Gen FIM
Next-Gen FIM provides security functionality that goes far beyond what the industry has come to expect from FIM tools. Some of the most immediately apparent benefits include:
- Blocking most threats at their source.
- Instantly ‘healing’ files and settings to their trusted state.
- Getting deep insight into the state of any asset or system.
- Cutting incident response time with thorough forensic evidence.
- Reducing remediation time and costs.
However, as valuable as these benefits are, there’s far more to the story. For a full rundown of what next-gen FIM is, how it works, and the benefits it provides, visit our new Next-Gen FIM resource page.

April 27, 2023