Are your cybersecurity measures up to snuff? If you don’t have a comprehensive way to assess your cybersecurity posture, you may not know until it’s too late.
Cybersecurity efforts are more vital now than ever before. Cyber attacks are becoming bolder and more sophisticated. As a result, you need to ensure your cybersecurity measures are sophisticated and robust enough to counter them. But how can you know if your security measures are strong enough?
Let’s look at the five steps you can follow to assess your cybersecurity posture. After reading, you should have the necessary information to assess your cybersecurity standing and make any necessary adjustments.
Why Assess Your Cybersecurity Posture?
You need to understand your cybersecurity posture before you can properly assess it. Therefore, we must begin this post by answering: What is cybersecurity posture? Cybersecurity posture encompasses all your processes and practices for preventing cyberattacks and your degree of preparedness in responding to and recovering from an attack.
Think of your cybersecurity posture the same way a fighter may view their boxing stance. All positioning that enhances your ability to defend against and respond to attacks is included in your cybersecurity posture.
Related: What is Trust in Cybersecurity, and Why Can't We Assume It?
You must regularly assess your cybersecurity posture for multiple reasons:
- Ensure Network Protection: The first reason to assess your cybersecurity posture is that this practice helps you identify weaknesses in your cybersecurity processes and systems that an attacker may exploit. By identifying these proactively, you can take steps to close any identified gaps and keep your data secure.
- Determine Future Projects: Identifying challenges or weaknesses in your cybersecurity posture can help guide your cybersecurity strategies, implementations, and projects. You can make plans to improve by identifying areas in need of improvement.
- Allocate Spending: Lastly, a cybersecurity posture assessment can show you where you may lack the tools or expertise to adequately protect your network. The results of your posture assessment may result in hiring decisions or implementing a new tool.
If you fail to assess your cybersecurity posture, you may leave your network open to vulnerabilities that cybercriminals can exploit. Additionally, you miss a critical opportunity to understand where your organization can improve its cybersecurity efforts.
5 Steps to Assess Your Cybersecurity Posture
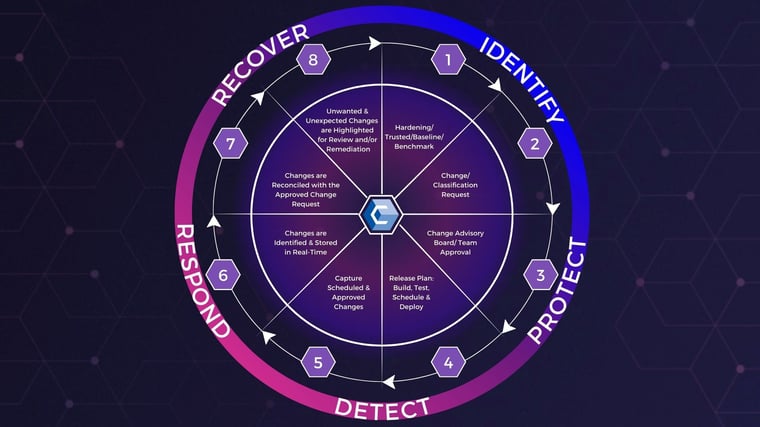
1. Take Inventory of your IT Assets
Step one in your cybersecurity posture assessment is to take inventory of all IT assets. You must do this first because you cannot adequately protect assets you are unaware of. Catalog all your IT assets, including:
- Physical assets like computers, servers, and mobile devices.
- Cloud and mobile applications your organization uses to conduct business and store data.
- Third-party assets housed on other company servers your organization utilizes during business.
Once you have a full understanding of all the IT assets you must evaluate in your assessment, you are ready to examine your security controls.
2. Examine Current Security Controls
You are already taking steps to protect your network and your organization’s data. Step two of your cybersecurity posture assessment is to examine those steps.
Some measures you may have in place in your organization include:
- Firewalls
- Intrusion Detection Systems IDS and HIDS
- Security Information and Event Management Systems (SIEMS)
It is important to note that you are not simply inventorying these measures. In addition to examining what measures are in place, you must also examine their current effectiveness.
Related: Applying CIS Benchmarks to Boost Security, Integrity, and Compliance
With these baselines established, you will be ready to move forward and choose an assessment method.
3. Choose Your Assessment Method(s)
Your assessment strategy can take multiple forms. You may choose to use one or multiple methods throughout your assessment. The list below is not exhaustive but includes many top strategies and methods for assessing your cybersecurity posture.
- IT Audits: Audit your tools and controls to identify possible challenges with your technology stack and how your tools have been implemented and integrated.
- Compliance Audits: Continuous compliance is the goal. Examining your current processes and positioning concerning the requirements you must follow is another assessment method you may choose.
- Security Training: Conducting pre-testing for security training with your employees can give you a clearer picture of how well-positioned the people in your organization are to protect themselves—and your organization—against socially engineered threats.
- Disaster Recovery Planning: Is your organization prepared to recover from interruptions or breaches? You should work to identify critical assets so you can make a recovery plan.
- Hiring an Outside Consultant: You may not have all the expertise needed to conduct an adequate assessment in-house. In this case, you should explore hiring an outside consultant capable of examining your organization’s processes and assets.
Once you’ve chosen your assessment method or methods, your next still is to assess possible attack vectors.
4. Assess Attack Vectors
What are attack vectors? An attack vector is any entry point or method an attacker can use to successfully breach your network. To fully understand your cybersecurity posture, you need to understand the angles from which cybercriminals may attempt to circumvent your defenses.
Some examples of attack vectors include:
- Malware
- Ransomware
- Phishing
- File encryption
- Distributed Denial of Service (DDoS) Attacks
- Insider Threats
- Insufficient Cloud Security
An important note regarding attack vectors is that some target your systems, while others, like phishing, are designed to attack your users directly. You should not neglect either approach in this step of your posture assessment.
After analyzing the above, you should have a good idea of the weaknesses in your current system. At this point in your assessment, you should be ready to begin outlining all necessary improvements.
5. Map Necessary Improvements
Examine the results of steps one through four of your cybersecurity posture assessment. Use your information to identify where your system and processes are most vulnerable to breaches. You can then use these insights to map out necessary improvements.
Your improvements may be related to your users, involving increased training to ward against social engineering attacks. Alternately (or additionally), you may need system or access changes, including implementing a File Integrity Monitoring solution like CimTrak to help you detect a change and remediate changes across your enterprise.
Some specific steps you may elect to take during this portion of your assessment include:
- Establishing employee training policies and procedures: Conducting regular training and updating employees on cybersecurity threats can help improve your posture concerning socially engineered attacks.
- Define policies for responding to security incidents: Employees will be more likely to respond appropriately to a security incident if they have clear steps to follow in the event of a suspected breach.
- Automating best practices for cyber hygiene: In addition to training, you will also want to practice good cyber hygiene practices like strong passwords, multi-factor authentication, and automated software updates.
- Vendor/third-party risk management as part of real-time monitoring procedures: Detect and roll back changes in real-time with a tool like CimTrak.
Improving Your Cybersecurity Posture
Following the five steps outlined in this post will give you the path you need to improve your organization’s cybersecurity posture. However, an assessment alone isn’t enough to keep your data safe from breaches.
Implementing a file integrity monitoring tool with system integrity assurance is a step to help ensure your organization’s data and systems are protected. System integrity assurance takes file integrity monitoring to the next level, reducing change noise while providing you with the important alerts you need every time.
Check out an instant preview of the CimTrak Integrity Suite, a file integrity monitoring solution with system integrity assurance, to see how you can improve your cybersecurity posture.
Tags:
Cybersecurity
October 20, 2022




![Reviewing the 5 Stages of the Cybersecurity Lifecycle [+ EXAMPLES]](https://www.cimcor.com/hs-fs/hubfs/Cybersecurity%20Lifecycle.jpg?width=520&height=294&name=Cybersecurity%20Lifecycle.jpg)