Any cybersecurity professional knows your security efforts aren’t “one and done.” Cybersecurity measures are continual, as you must constantly monitor your network for breaches and threats that could harm your data and your organization.
An attacker gains access to your network. You know you need to recover from this breach as quickly as possible, but what steps do you take to detect and rebuff the attacker? Then, what comes after to ensure you can retain business continuity in the face of the breach?
This post will examine the phases of the cybersecurity lifecycle in more detail, giving you the information you need to comply with NIST standards.
Phases of the Cybersecurity Lifecycle
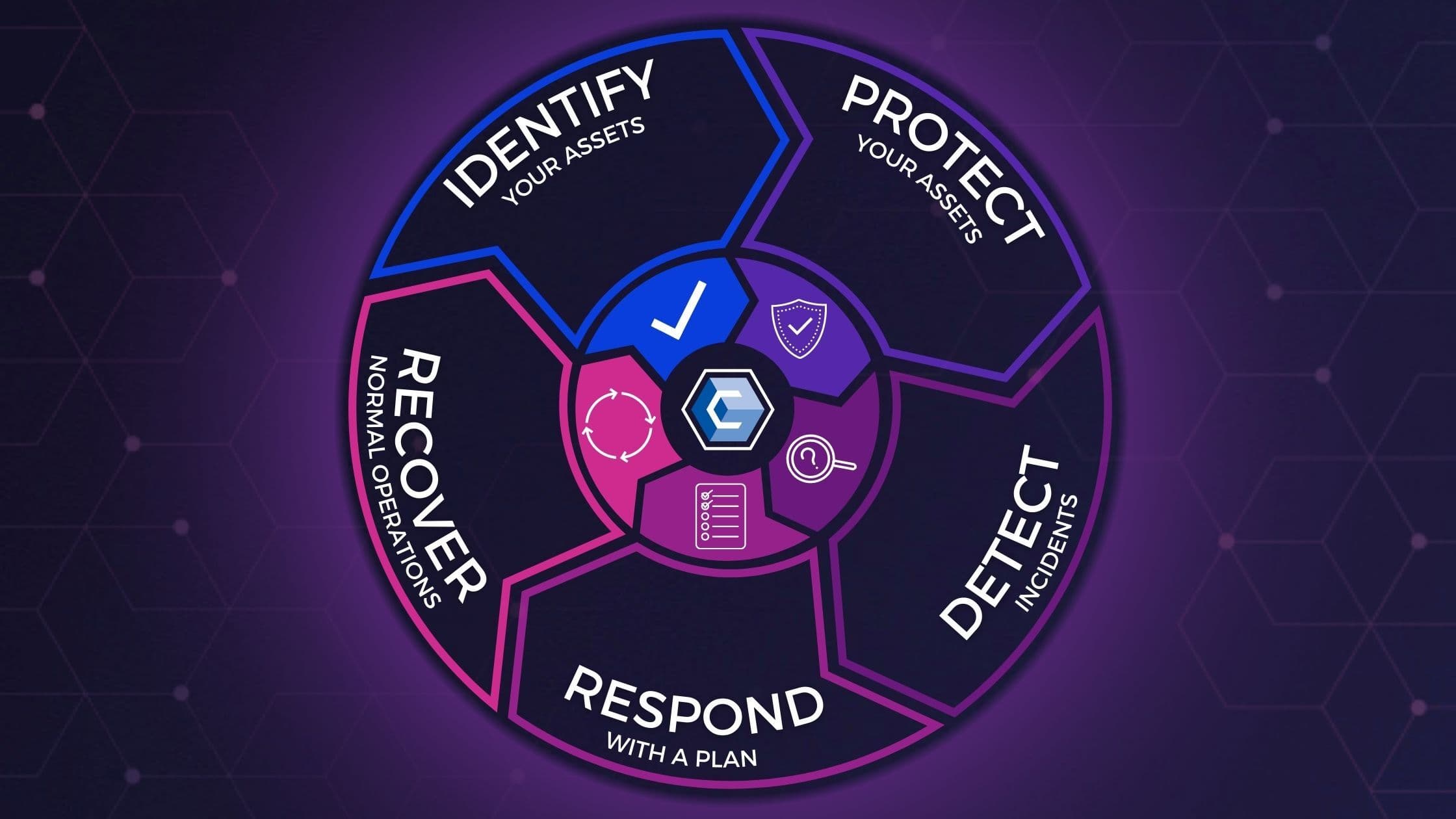
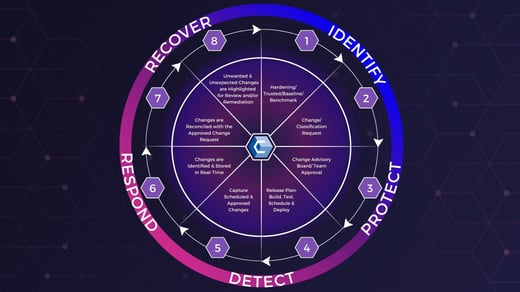
As defined by the National Institute of Standards and Technology (NIST), the Cybersecurity Framework's five Functions—Identify, Protect, Detect, Respond, and Recover—are built upon the components of the framework model.
The five functions act as a backbone around which other framework core elements are organized. They represent the primary pillars of a successful and holistic cybersecurity program. Additionally, they can help organizations by easily expressing their management of cybersecurity risk at a high level and enabling risk management decisions.
Ultimately, these functions parallel the cybersecurity lifecycle. Following the cybersecurity lifecycle regarding your security efforts can help your organization better understand your positioning and risk. Additionally, a firm understanding of the cybersecurity lifecycle stages will give you a roadmap to follow regarding your remediation efforts in the event of a breach.
Related: What Can Cybersecurity Learn from IT?
Let us now examine each stage of the cybersecurity lifecycle in detail.
Secure your enterprise and get compliant today. Skip ahead for a customized demo of CimTrak.
1. Identify
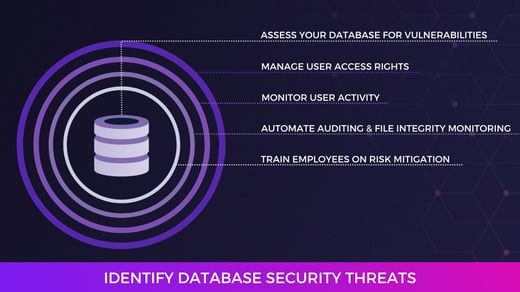
The first stage of the cybersecurity lifecycle is the identification stage. During this stage, you must take steps to catalog and comprehend the systems, assets, and people who comprise and influence your network and its security.
Additionally, you should consider the business context, players, and resources necessary to maintain business continuity. NIST provides several examples of activities that may occur during this stage. A few of these examples include:
- Identifying physical and software assets within your organization and establishing asset management processes.
- Identifying cybersecurity policies and ensuring they comply with legal and regulatory requirements.
- Identifying vulnerabilities, threats, and risk-response activities through a Risk Assessment.
At this stage in the cybersecurity lifecycle, your organization may engage in activities such as performing an inventory of all your IT assets and setting up monitoring processes to track user access and behavior.
2. Protect
In the Protect stage of the cybersecurity lifecycle, your organization must take steps to defend your data and assets. This phase outlines the processes you must implement to ensure your organization can limit the detrimental impact of a breach.
Related: 6 Warning Signs of a Data Breach in Progress
Some NIST examples of activities you may engage in at the Protect stage include:
- Providing staff with cybersecurity training based on their role and system privileges.
- Implementing access controls and identity management processes.
- Protecting resources and assets through maintenance.
Your organization can successfully manage the Protect state of the lifecycle by utilizing cybersecurity tools and solutions like firewalls, VPNs, and file integrity monitoring software.
3. Detect
Stage three of the lifecycle is the Detect stage. This stage involves promptly discovering breaches and other cybersecurity events. Given the sophistication of modern cybercriminals, you should operate under the assumption that a breach is inevitable. In this case, prompt detection of that breach is vital to the security of your network.
Related: Change Monitoring vs. Control vs. Management: What's the Difference?
NIST provides several examples of activities related to the Detect stage:
- Implementing continuous monitoring of your network and user activities.
- Consistently verifying the effectiveness of protective measures in your network.
- Evaluating your awareness of unusual behavior and events and maintaining processes designed to detect those events.
Your organization can succeed in the Detect stage of the cybersecurity lifecycle by creating a policy for logging system activity and user access. Implementing a tool like CimTrak can help automatically create this audit trail. Additionally, CimTrak assists your team in flagging unusual activity so that you can take action quickly.
4. Respond
After detecting an anomaly or a breach, your organization must take action. This action falls under stage four of the cybersecurity lifecycle: the Respond stage. Your organization’s ability to contain and mitigate the impact of a breach is dictated by your actions during this stage.
Some of NIST’s examples of actions in the Respond stage include:
- Communicating clearly with stakeholders, law enforcement, and other parties where appropriate during and after a breach.
- Performing mitigating actions to prevent the spread of a breach and halt lateral movement within your network.
- Consistently improving and learning after an event to prevent future breaches of the same nature.
A fundamental step in preparing for this lifecycle stage is creating a cyber incident response plan (CIRP). This plan should clearly outline the steps staff must take in the event of a cybersecurity event.
A solution like CimTrak also supports this stage. CimTrak not only helps to detect unauthorized changes in your network but can also automatically roll back these changes to set you up for successful recovery from the event.
5. Recover
The final stage of the cybersecurity lifecycle is the Recover stage. In this stage, you will set up the systems and practices to restore full functionality after a breach. When you master this lifecycle stage, you can quickly return to normal operations and performance following a cybersecurity event.
NIST examples of recovery stage activities include:
- Setting up Recovery Planning processes and procedures ahead of time.
- Adjusting processes and implementing new solutions based on lessons learned from previous challenges.
- Coordinating communication internally and externally following an incident.
Setting up a recovery plan is the best step to set your organization up for success in the Recover stage of the cybersecurity lifecycle. Ensure that staff at all levels of your organization understand what they can do to help return to business as usual after a breach.
Managing Your Cybersecurity Lifecycle
By studying the five stages of the cybersecurity lifecycle, you can apply this framework to help with cybersecurity challenges you may face. However, to properly manage and maintain your cybersecurity lifecycle, you’ll need more than understanding: You’ll need the right tools.
CimTrak can help continuously monitor your network for breaches, threats, and other potential problems. With the help of CimTrak’s file integrity monitoring software with system integrity assurance, you can easily achieve a continuously secure and compliant IT infrastructure.
CimTrak can help with every stage of the cybersecurity lifecycle. Some of the elements our solution helps with include:
- Compliance and Auditing: Continuous compliance with prescriptive steps to remediate failed systems ensuring they are in a trusted and expected state.
- Risk Management: CimTrak operates in real-time, enabling Mean-Time-To-Identify (MTTI) security incidents in seconds.
- Manage VulnerabilitiesMonitors your environment and doesn’t allow unauthorized access to your routers, firewalls, and network devices.
- NIST 800-171 Compliance: Assist with control categories::
- 3.1 Access Control (AC)
- 3.3 Audit and Accountability (AU)
- 3.4 Configuration Management (CM)
- 3.8 Media Protection (MP)
- 3.11 Risk Assessment (RA)
- 3.12 Security Assessment (CA)
- 3.13 System and Communications Protection (SC)
- 3.14 System and Information Integrity (SI)
Get a customized demo of CimTrak today to see how our solution can help your organization get secure and stay compliant.
Tags:
Cybersecurity
October 17, 2024