In a significant development for the defense contracting industry, the Department of Defense (DoD) is set to roll out CMMC 2.0, a revamped version of the Cybersecurity Maturity Model Certification. The new regulation, outlined in a proposed rule change to the Defense Federal Acquisition Regulation (DFARs), seeks to reduce the burden on contractors by paring down cybersecurity requirements. This move aims to strike a balance between enhancing cybersecurity standards and minimizing obstacles for businesses, particularly smaller ones, in meeting DoD compliance requirements.
Changes in Scope and Expectations
One of the primary changes in CMMC 2.0 is the elimination of security levels two and four, effectively reducing the number of security tiers from five to three. Most notably, contractors that do not handle controlled unclassified data will no longer be mandated to obtain a third-party certification. This shift is expected to alleviate the financial strain on thousands of contractors, as they no longer have to bear the cost of unnecessary certifications.
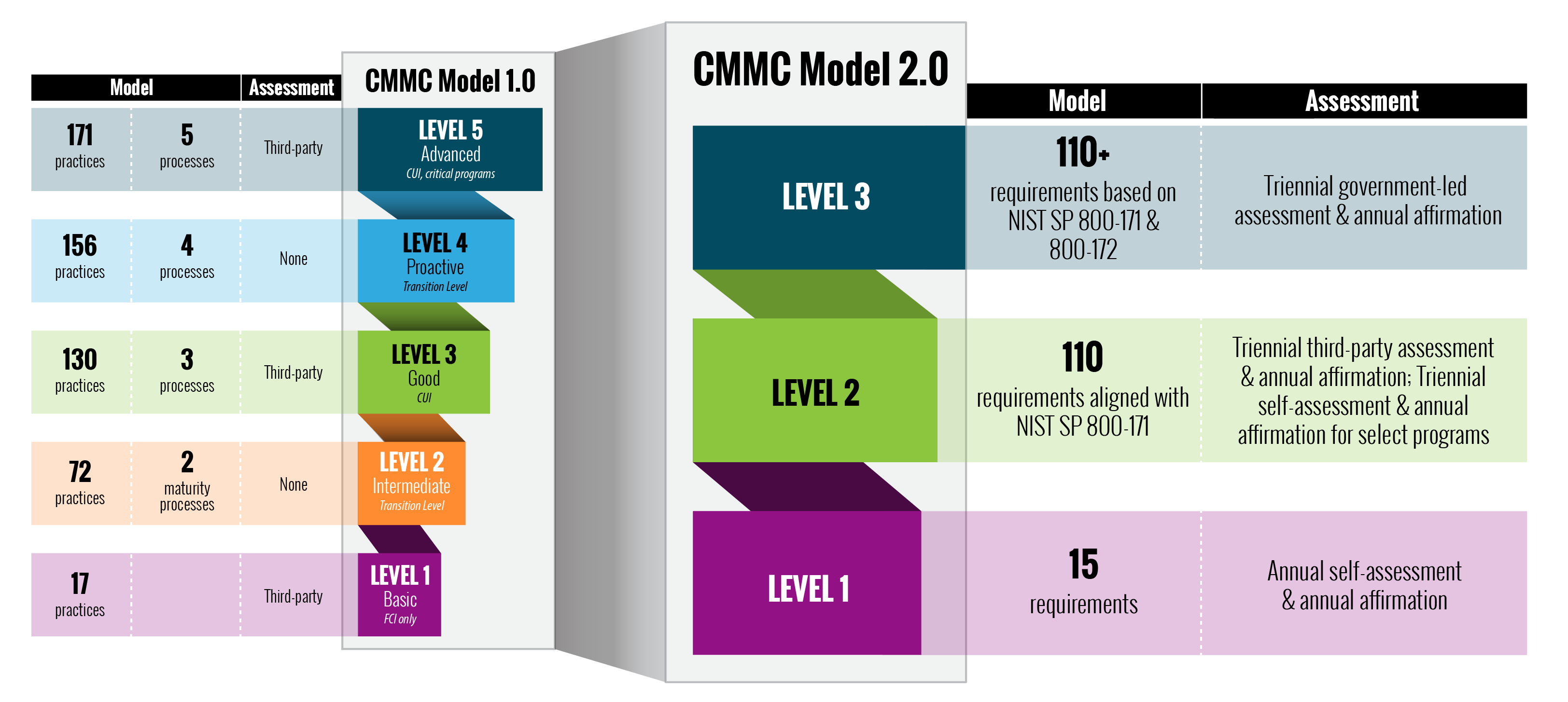
Level three contractors dealing with controlled unclassified information (CUI) will see a bifurcation, with only prioritized contracts requiring third-party assessments. The introduction of a self-assessment protocol, aligned with the current DOD acquisition protocol, allows certain level three contractors to certify themselves, further streamlining the compliance process.
Plan of Action and Milestone (PoAM) reports will now be accepted, allowing contractors to showcase their commitment to meeting security controls over time. This flexibility acknowledges that achieving full compliance may take time, preventing contractors from being disqualified solely due to temporary shortcomings.
CMMC and NIST 800-171 R2 vs R3
Despite the curiosity within the Defense Industrial Base (DIB) about the potential effects of 800-171 r3 on their compliance requirements, any contractor with a DFARS 7012 clause in their contract is obligated to adhere to NIST 800-171 r2. 800-171r3 is currently in the Initial Public Draft period until January 24th, 2024, and is not anticipated to bring any immediate changes to CMMC 2.0. Subsequently, NIST will review and address the comments, responding publicly and implementing revisions as necessary. NIST has announced their anticipation of the final release of 800-171r3 in Spring 2024.
Presently, NIST 800-171 r2 comprises 110 controls that must be fulfilled for compliance. In the case of NIST 800-171 r3, the number of controls has decreased to 95. It is crucial to emphasize that meeting controls involves satisfying all assessment objectives associated with each control. In the context of 800-171 r2, 320 assessment objectives must be addressed to fulfill the 110 controls. However, with 800-171 r3, roughly 445 assessment objectives must be satisfied to meet the 95 controls. Although some controls from Revision 2 have been integrated into other controls in Revision 3, it is noteworthy that, despite the reduction in controls, the assessment process will be more demanding, requiring compliance with over 40% more assessment objectives.
Broader Waiver Process and Industry Impact
CMMC 2.0 introduces a broader waiver process for contractors, adding an extra layer of flexibility. The goal is to establish a more collaborative relationship between the DoD and industry players, fostering a supportive environment for adopting robust cybersecurity practices.
While these changes aim to benefit defense contractors, there are broader implications for the ecosystem of assessors, consultants, trainers, and cyber experts. With a potential reduction in demand for assessments, the strain on the CMMC Accreditation Body (CMMC AB) and its accredited assessors may be alleviated. However, concerns have been raised about the availability of certified assessors, the tight labor market, and the need for more qualified professionals.
Legal Implications and Future Considerations
Despite the positive aspects of CMMC 2.0, questions linger about its precise nature. Allowing businesses to self-certify at CMMC level one may open the door to False Claims Act litigation. The potential for whistleblowers to exploit loopholes in the self-certification process poses a challenge that the DoD and contractors must be prepared to address.
Many have sought clarity on CMMC implementation, and the evolution to CMMC 2.0 signals a responsive approach to feedback and concerns. The changes aim to balance the need for heightened cybersecurity standards with practicality, recognizing defense contractors' diverse landscape and varying levels of involvement with sensitive data.
How CimTrak Can Help
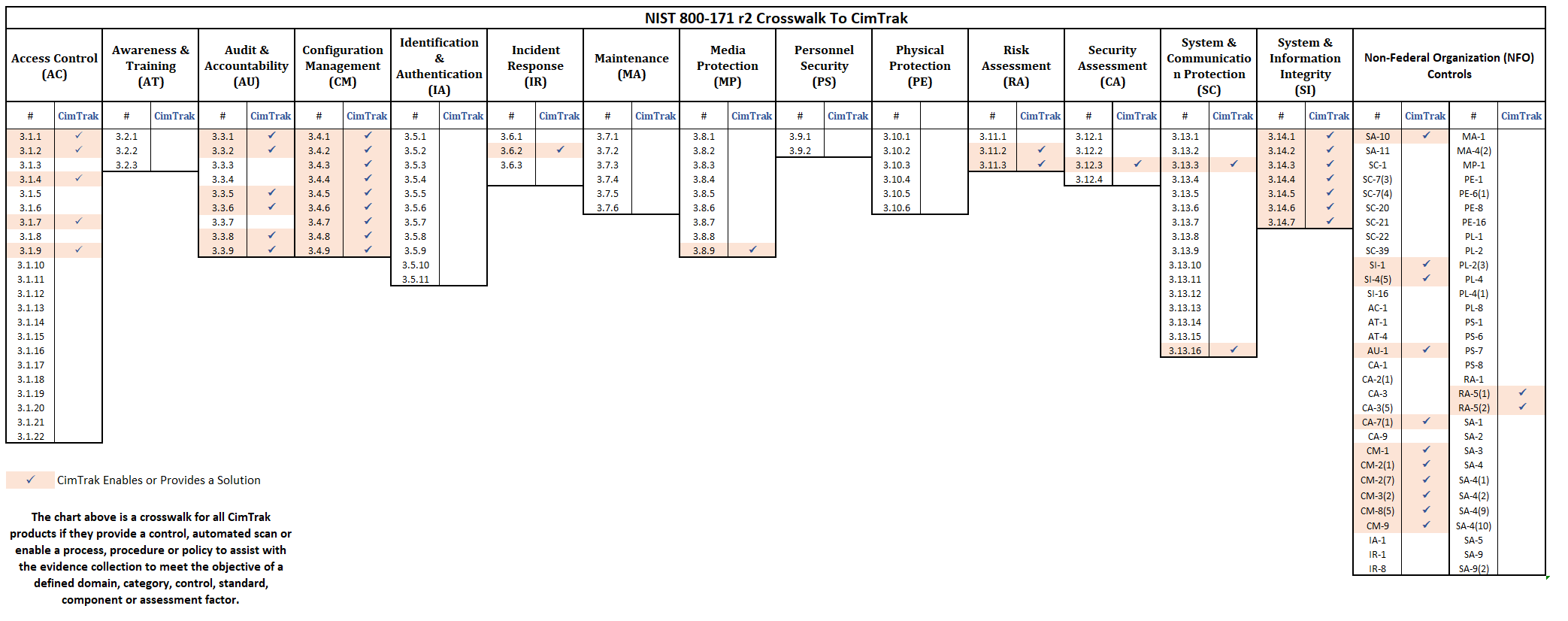
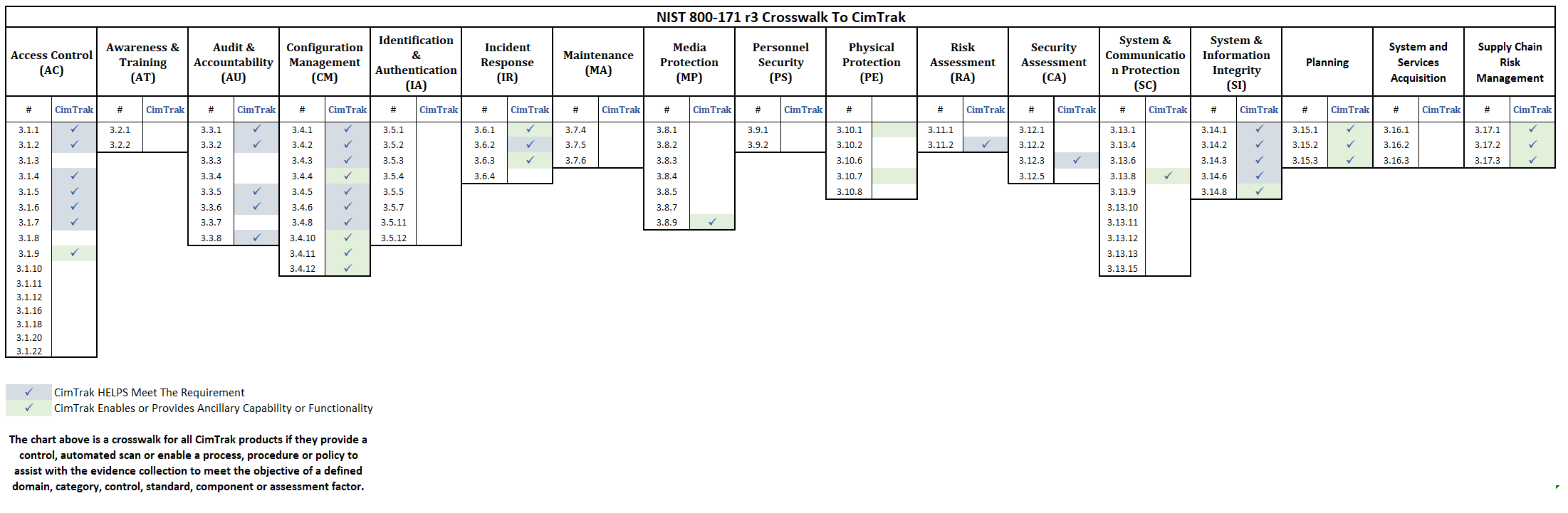
Meeting the compliance objectives of CMMC 2.0 will become a moving target in the coming months as 800-171r3 is finalized this spring. That said, crosswalks are provided for both R2 and R3 to help ease the burden of understanding where and how CimTrak can provide control, automated scan, or enable a process, procedure, or policy to assist in the evidence collection to meet both requirements.
CimTrak Crosswalk with NIST 800-171 r2
CimTrak Crosswalk with NIST 800-171 r3
CMMC 2.0 marks a significant milestone in the ongoing efforts to enhance cybersecurity across the defense industrial base. The DoD aims to foster a collaborative relationship with industry players by refining the certification process and easing the compliance burden. As the defense contracting landscape evolves, ongoing dialogue and adaptation will be crucial to ensure cybersecurity measures' continued effectiveness and relevance in a rapidly changing digital environment.
For more information on how CimTrak can help your organization prepare for the upcoming changes, contact one of our security experts today!
Tags:

January 25, 2024




