Ransomware: Part I
When hearing the term “ransom”, you might imagine the old threatening letters patched together from magazine cut-outs that may convey a message similar to “Pay up or else.” In the digital world, ransomware is the same concept and can be just as frightening. In this 2-part series we will discuss what ransomware is, and steps that can be taken to fight the battle.
Why the Concern About Ransomware
Ransomware is one of the worst forms of malware you can get. When it covertly infects a computer or phone, it will encrypt your personal data like photos, videos, documents, and more. Thus you won’t be able to access or decrypt this data unless you pay the hacker who caused the damage to you. Typically, hackers will try to disguise themselves as the FBI, legit Anti-Virus tools, or some other professional agency.
Unless you pay these anonymous thieves their ransom in Bitcoin (an untraceable, anonymous, cryptocurrency) your data is gone forever. Even then, this is under the assumption the cybercriminal, who thought it was a good idea to hold your personal data ransom in the first place, will be kind enough and give back your data after paying the large lump sum of money.
Popular ransomware detected out in the wild is the FBI MoneyPak Ransomware. In many cases, the hacker tries to make this warning seem real by displaying the FBI logo and a deceptive-looking website. The warning states,
“You have been subjected to a violation of Copyright and Related Rights Law (Video, Music, Software) and illegally using or distributing copyrighted contents, thus infringing Article 1, Section 8, Clause 8, also known as the Copyright of the Criminal Code of the United States of America. To unlock your computer and to avoid other legal consequences, you are obliged to pay a release fee of $300. Payable through GreenDot MoneyPak.”
Though it can carry a high degree of merit, if you have downloaded content stated by the warning, it doesn’t really make sense for the government to ask you to pay with an untraceable prepaid credit card service. Regardless of whether or not you believe the actions will occur, your files are locked until you pay the ransom.
Other ransomware may not try to disguise themselves as any authority but rather tell you forthrightly that your files are locked and encrypted and in turn, you must pay in Bitcoin to get access to your data again.
Where Ransomware is Heading
In 2015, more than 2,000 complaints were received by the FBI regarding ransomware. Just last year alone, victims paid the ransoms; totaling more than $20 million. As this is becoming such a large problem, companies are now being attacked with ransomware and losing so much important information, the only choice is to pay up.
If they fail to do so before the timer hits zero, the corruption could disrupt regular operations, lose sensitive or proprietary information, expose classified documents, incur huge financial losses, harm the organization's reputation, or worse. Hollywood Presbyterian Hospital paid a $17,000 ransom earlier this year. One month later MedStar’s 10-hospital network was compromised for close to a week, with a confirmed ransomware attack. In April 2016, the FBI noted that hospitals, the education sector, and government agencies are just some of the entities impacted recently by ransomware.
As with large and small entities, including corporations within all industries targeted, experts warn personal devices partnered with work devices are not the safer choice. Ransomware is being spread via email, freeware, websites, downloads, and more to home computers and unsusceptible users. As many organizations are utilizing software for monitoring, monitoring for unalterable files is the only way to stop ransomware.
Where to Begin
With CimTrak in your environment you are able to completely lock down critical data, and the “Deny Access Mode” stops all file additions, removals, or modifications. Regardless of what permissions a user might have or what type of account you are logged in with, no person or process will be able to change files. CimTrak’s change log shows how the CimTrak 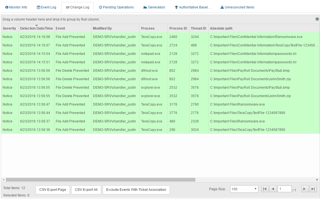 Agent actually blocks specific attempted file changes. These same events could be sent off to Email, SMS, Syslog, or SIEM solutions. The moment ransomware fails at multiple attempts to steal data, you will be notified and have forensic data for that event.
Agent actually blocks specific attempted file changes. These same events could be sent off to Email, SMS, Syslog, or SIEM solutions. The moment ransomware fails at multiple attempts to steal data, you will be notified and have forensic data for that event.
Additionally, CimTrak now integrates with VirusTotal, a subsidiary of Google, which identifies viruses, worms, trojans, and other kinds of malicious content detected by antivirus engines and website scanners. You can easily right-click a file within CimTrak and analyze the file to see if it is a threat or not. This greatly helps users understand not only what is changing in their environment but if these files are threats or not. In Part II of Ransomware, we will dig deeper within the CimTrak agent and show you how to analyze and fight ransomware.
You can protect your critical files from ransomware using a next-generation FIM such as CimTrak. Download our technical summary to learn more today.
Tags:
Cybersecurity
June 29, 2016




