Before diving into how to mitigate the human factors of cybersecurity, perhaps it is best to understand what the term actually represents. The human factors of cybersecurity represent the actions or events when human error results in a successful hack or data breach. Now, you may have the impression that hackers are simply looking for a weak entry point that naturally exists within a system. However, more often than not, they find a weak link that was caused by human hands.
According to Verizon’s 2022 Data Breach Investigations Report, human error accounted for 82% of data breaches. Sharing of passwords, poor patch management, double-clicking on unsafe URLs, and organizational access through a personal device are just a few human errors that lead to a security threat, many of which could be mitigated.
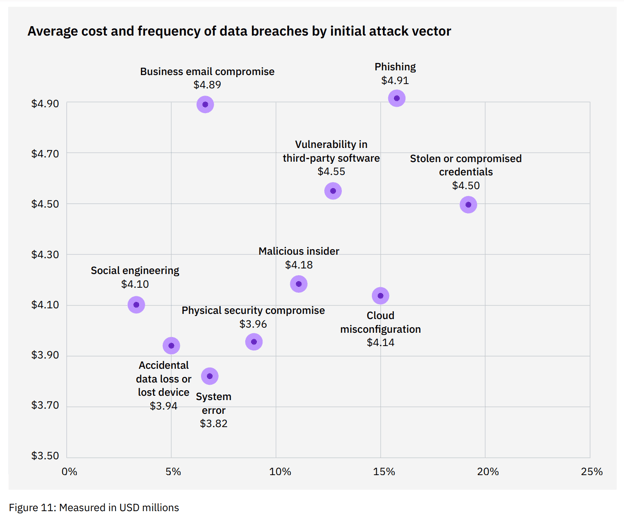
Source: IBM Security: Cost of a Data Breach Report 2022
But why should you care?
Besides the security of your customer’s information and the life of your website, cyber hacks can prove to be very costly for not only your reputation but also your bottom line. In 2022, IBM and the Ponemon Institute found the average cost of a data breach has hit a record high of $4.35 million. That’s a good chunk of change for actions or events that could be avoided with the right tool.
So what can you do to mitigate the easily avoidable human factor of cybersecurity? Here are three easy tips to get you started.
1. Educate Your Employees about Social Engineering
There are many ways someone can break into your system through social engineering. Social engineering is the use of media to manipulate people into giving up confidential information. With up to 90% of malicious breaches resulting from social engineering attacks, your organization would no doubt benefit from providing regular cybersecurity awareness training. Here are some examples of social engineering to share with your employees:
-
- Spear Phishing is a variation of phishing that reaches fewer victims but tends to be much more successful. Highly customized emails are typically sent to a much smaller number of potential victims and try to use familiarity to fool the victim into buying into the scam.
- Reverse Social Engineering may be similar to your favorite movie heist. For this particular strategy, a hacker will attack a company’s network and claim to have found the source of the hack in order to offer help in repairing it. If the help is accepted, the hacker will then have access to the system.
- The Friendly Hacker is a more recent style of social engineering that focuses on email or social media accounts. Here a hacker will try to access an account and search their messages for any kind of PDFs, video files, or other kinds of downloadable content. From there a malicious code can be embedded into another document, perhaps labeled as an “updated version,” and will then be sent to the unknowing victim to open. One key to take note of here is that the initial victim is not always the target, leaving higher-ranking employees vulnerable to attacks.
- Smishing (SMS phishing) is a form of phishing via the use of SMS text messages. Bad actors use spoofed phone numbers to either send out messages with malicious links or act as HR or an IT representative from your company requesting personal information or verification codes.
Looking to avoid and learn more about social engineering? Check out this article from our blog.
2. Require your Outside Vendors to Employ Strong IT Security
When you work with outside vendors, it is important to know they are just as secure (if not more secure) than your business. In 2017, the open-source software Equifax used to support its online dispute portal was exploited, resulting in hackers accessing the sensitive information of over 209,000 U.S. Equifax customers. Equifax eventually settled in a payout costing about $1.38 billion, proving that your business, no matter the size, could be just as vulnerable as your vendors. Therefore, it is important to communicate your concerns and ask about their surveillance process and monitoring software. If you’re unsure of the quality of their security, ask to see their IT infrastructure audits to insure that appropriate safeguards are in place. Lastly, you can strongly encourage them to utilize a change detection software to identify when any of their systems have been changed, for better or for worse.
3. Adopt a Zero Trust Strategy
Implementing a Zero Trust strategy can help your organization eliminate implicit trust and the potential risk of data loss by restricting employee access to only the data and applications needed to perform their work. This adds an additional layer of security by ensuring only the right people have access to the right resources at the right time.
A Zero Trust strategy adheres to three core principles:
- Assume breach - Always assume there is a malicious presence in your environment at all times and take the necessary measures to mitigate the threat.
- Verify, don’t trust - Organizations need to continuously verify all components of their IT infrastructure under the assumption that everything in the IT environment is malicious unless it has been expressly authorized.
- Least privilege - Users, devices, and services should be granted the minimum possible access to complete their function to minimize the potential impact of malicious activity.
Want to learn exactly how to implement a Zero Trust strategy? Check out this article from our blog.
4. Utilize a Change Detection Software
Change detection software, such as CimTrak, is a comprehensive security, integrity, and compliance application that is deployed and scales to the largest of global networks. This kind of automated software detects processes, flexible response options, and auditing capabilities to make it a powerful cyber security tool. It can also help you identify:
- Who made the change
- What changes were made
- Where the changes reside
- When the changes had taken place
- How the change was implemented
Better yet, CimTrak’s self-healing software can be used to revert unwanted changes back to their original form to avoid any downtime.
Thinking that your business could benefit from an added layer of security? Learn more by watching an instant preview.
Tags:
Cybersecurity
February 21, 2023